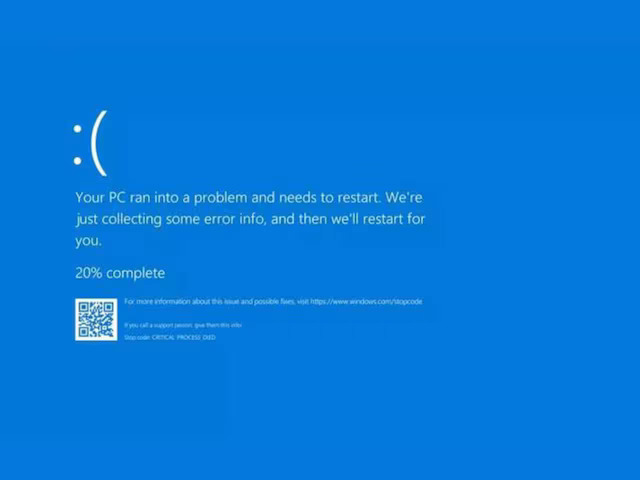
Opportunistic cyber criminals are exploiting the recent Microsoft outage caused by an error from cybersecurity firm CrowdStrike during an update. Security agencies are alerting organizations and individuals to the heightened risk of cyber attacks following the global crash of millions of machines on 19 July.
This pattern of exploitation is consistent with past incidents such as the 2024 UK General Election, the cost-of-living crisis, and the Covid-19 pandemic. These events have historically been targeted by malicious actors for phishing and other cyber attacks.
The UK’s National Cyber Security Centre (NCSC) has confirmed that the outages were not due to a security incident or malicious activity, but they still advise high alertness.
An increase in phishing attempts referencing the outage has been observed, targeting both organizations and individuals. The NCSC recommends reviewing its guidance to implement multi-layer phishing defenses and remaining vigilant against suspicious communications.
The United States Cybersecurity and Infrastructure Security Agency (CISA) supports the NCSC’s warnings, noting ongoing phishing attempts by cyber threat actors leveraging the outage.
CISA is actively collaborating with CrowdStrike and other partners to monitor and address emerging threats. Similarly, the Australian Cyber Security Centre (ACSC) has reported malicious websites and unofficial code claiming to offer recovery solutions for the outage.
Financially motivated threat actors are expected to exploit the confusion from the outage, according to researchers at ReliaQuest. They predict a surge in phishing campaigns and social engineering attacks aiming to compromise credentials and deploy malware.
ReliaQuest emphasizes the importance of following official remediation advice to mitigate these threats. Additionally, an individual falsely claiming responsibility for the incident was banned from a dark web forum for failing to provide proof.
CrowdStrike has identified instances of malicious code circulating, including a fake update named crowdstrike-hotfix.zip containing a HijackLoader payload that deploys the Remcos remote access Trojan (RAT).
This malicious file was first uploaded from Mexico during the outage. CrowdStrike also noted an increase in typo-squatting domains designed to trap users who mistype the company’s name. They advise ensuring communications with CrowdStrike through official channels and following their technical guidance.
