Key Insights:
- Whale dumps 12.16M ENA, realizing $817K loss, adding pressure on short-term price action.
- ENA risks drop to $0.259 as technicals weaken and support levels face retests.
- Despite selling, USDe supply surges $300M, signaling strong growth in Ethena ecosystem.
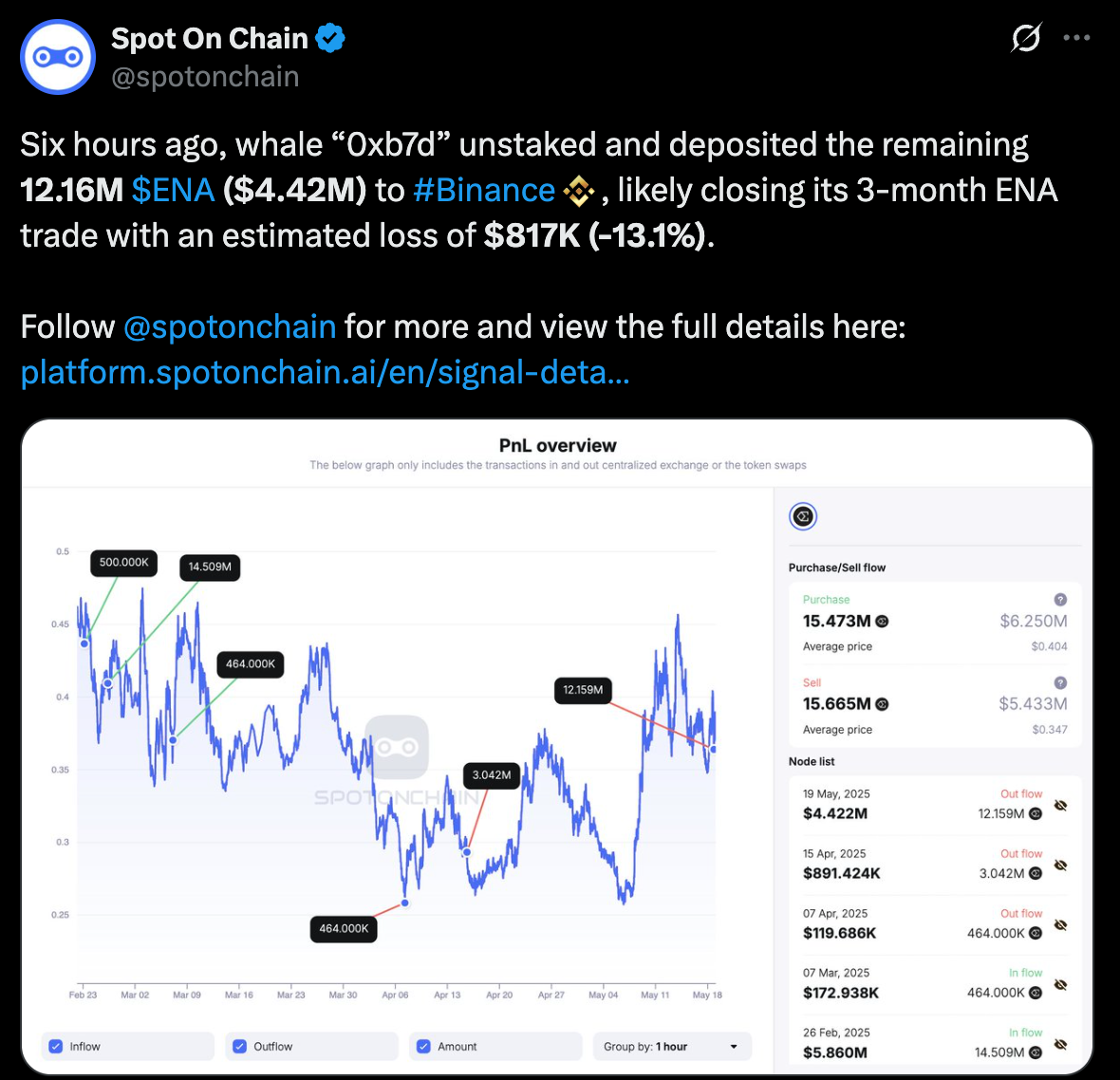
The price of Ethena’s ENA token has dropped after a large whale sold 12.16 million tokens valued at $4.42 million. According to Spot On Chain, the move seems to end a three-month trade that cost the company $817,000 or around -13.1%. This is one of the biggest losses on ENA for a single address in recent times.
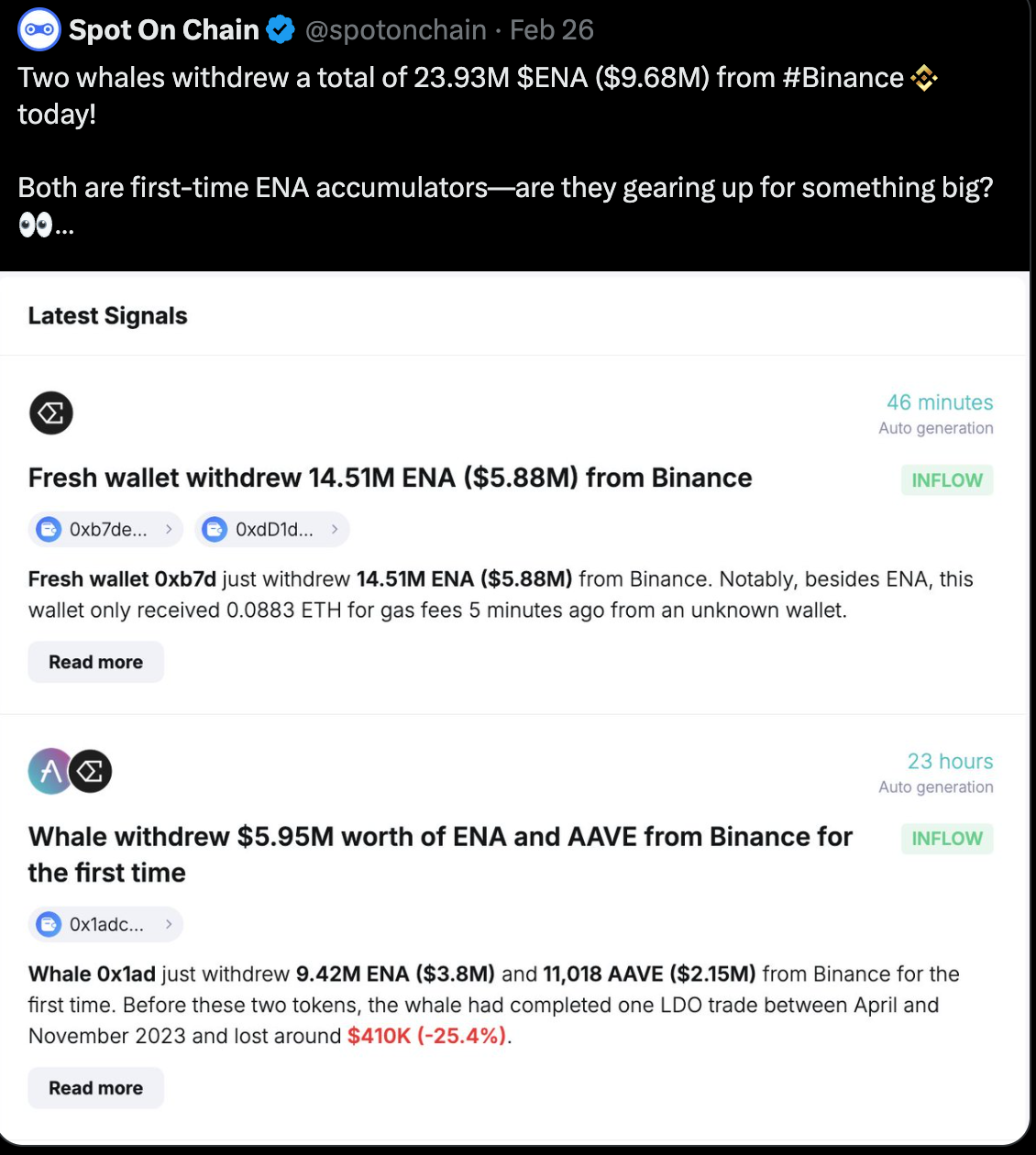
In February, the first record of wallet 0xb7d showed that it withdrew more than $5.8 million in ENA. In addition, another new wallet received $3.8 million in ENA and $2.15 million in AAVE. Together, they took out almost $10 million in ENA in just one day.
Such accumulations led to bullish optimism. But because of the May 18 deposit and realized loss, the original expectations did not happen. The PnL chart shows that the average price for buying was $0.404 and the average price for selling was $0.347.
At the same time, the price of ENA is returning to the $0.35 range. If a lot of big investors leave the market, there may still be high pressure on prices in the short run. As per recent technical analysis, $0.26 is the potential support level.
Leverage Trading Also Signals Broader Weakness
Meanwhile, another whale put in $10.1 million into Hyperliquid and took long positions with leverage on ENA, PEPE and NEAR. Still, the positions were closed before the market moved, causing a loss of $400,000. The wallet currently has a 5x leveraged position in HYPE and has also set up an open order for TIA.
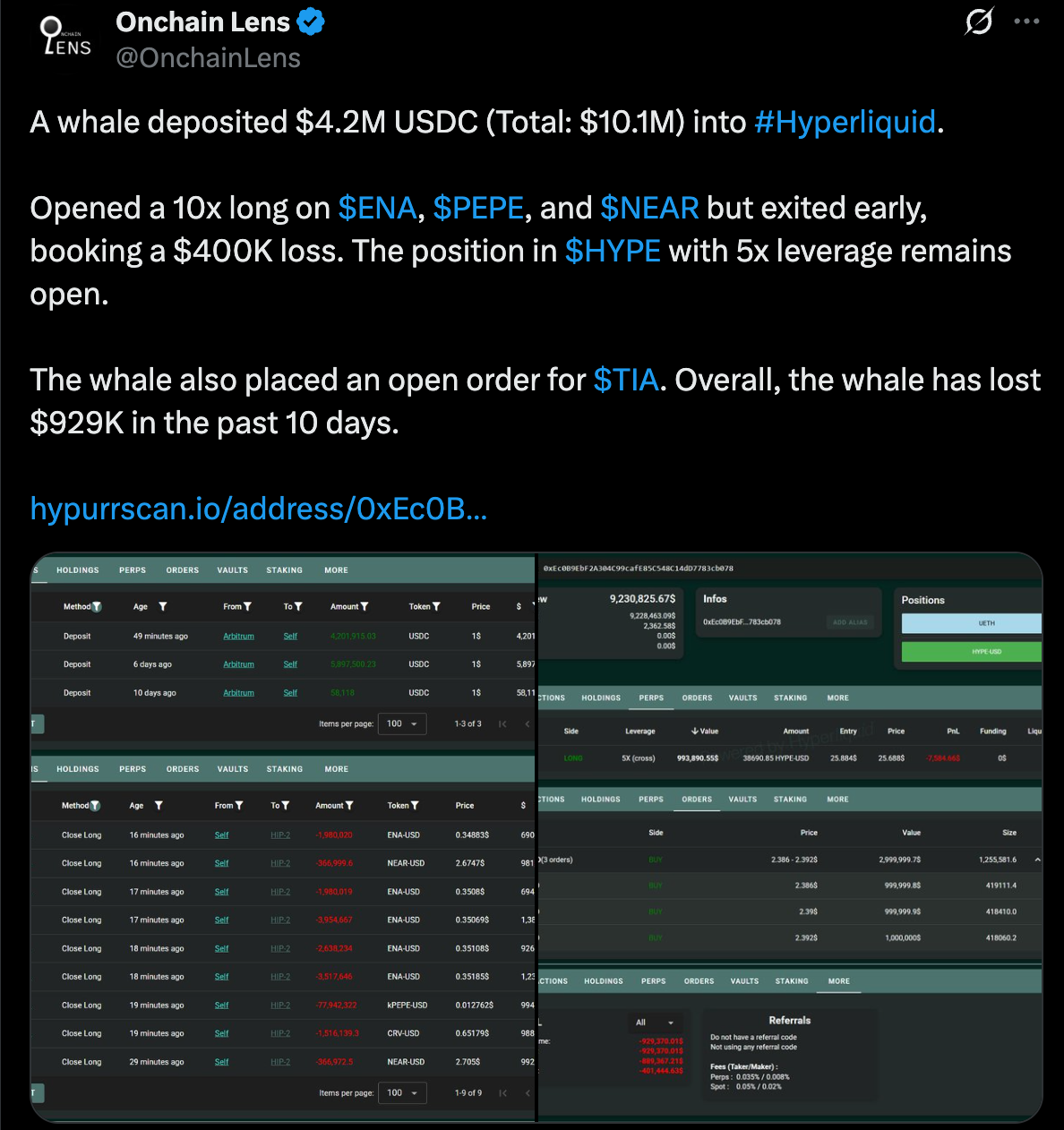
Onchain Lens reports that this trader has lost $929,000 during the past 10 days. The recent losses experienced by spot and leveraged traders are making people notice ENA’s short-term fluctuations. If the current selling reflects how people feel, it could lead to further declines.
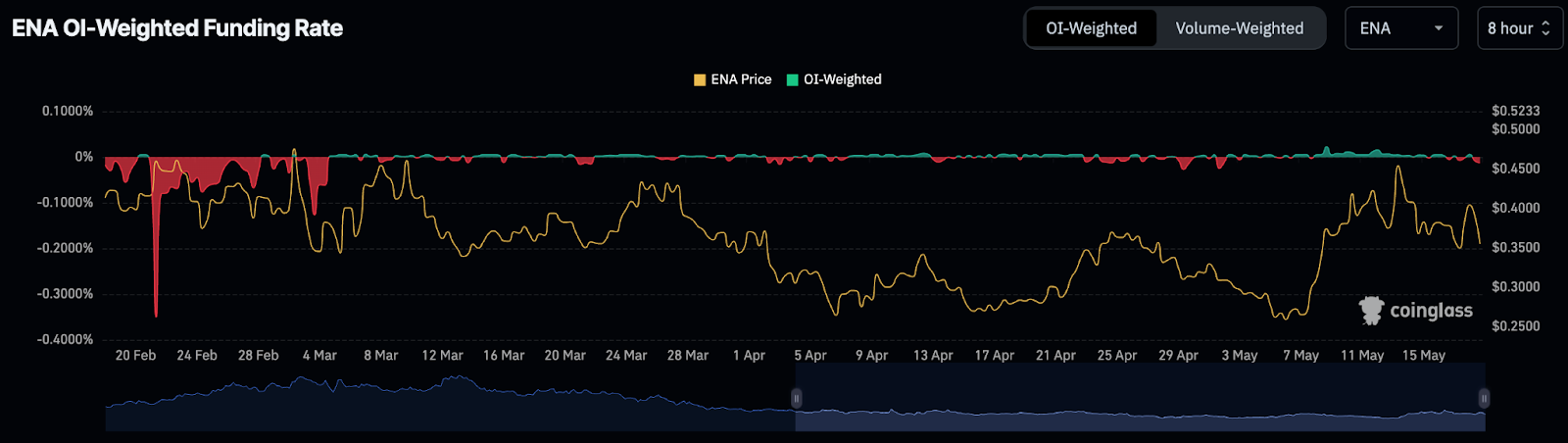
Furthermore, according to CoinGlass, the funding rate for ENA’s OI-weighted data has mostly been negative. Most of the time in March and April, rates were either unchanged or negative and prices were moving down. Traders seem to lack confidence in the market’s ability to rise further at the moment.
Technical Setup Suggests Retest of Lower Support
According to the 4-hour chart for ENA/USDT, the token is trading at $0.348, below the important level at $0.359. The price has gone past this level and has not returned to it yet. If ENA does not rise above this zone, the current trend could turn bearish.
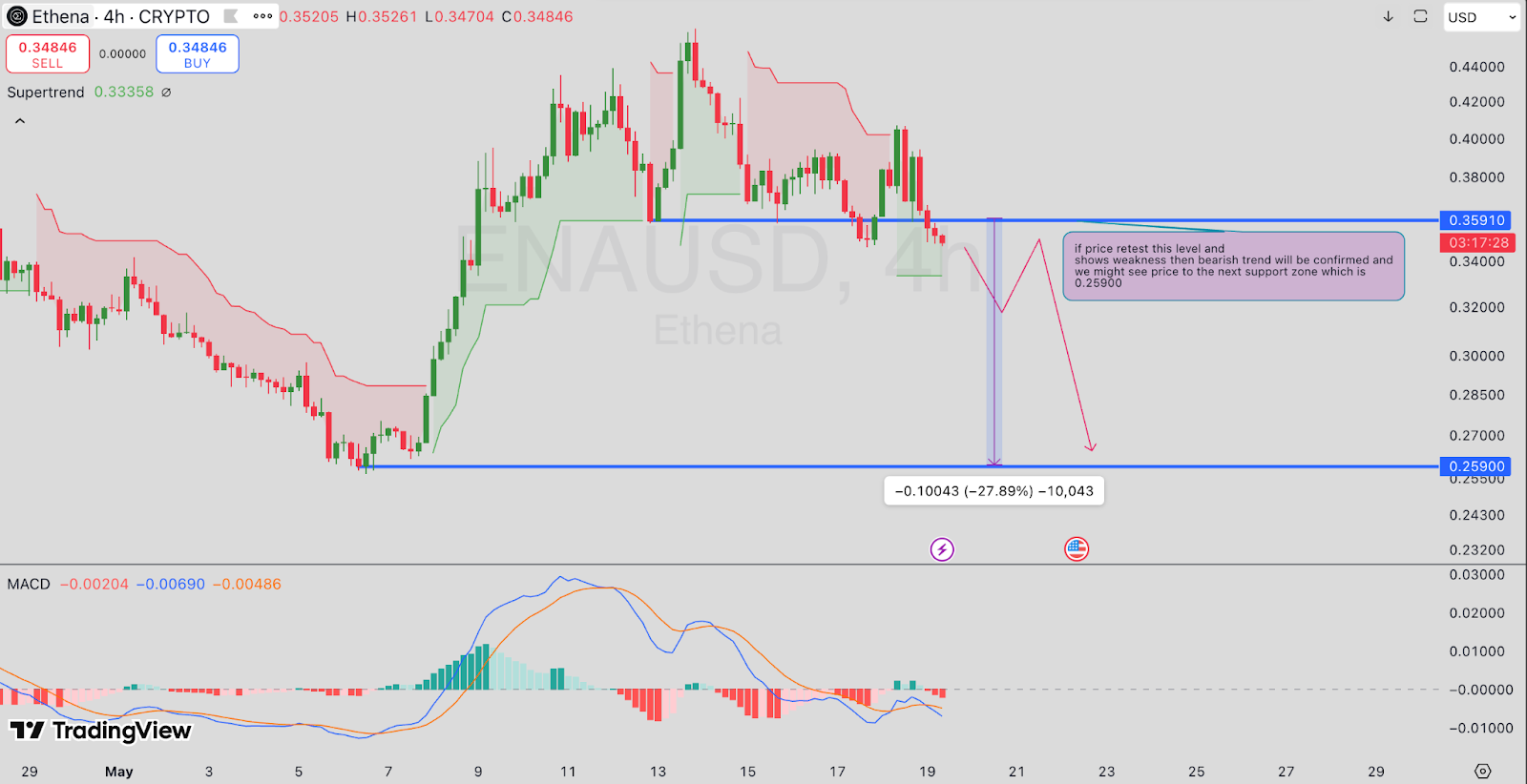
Moreover, the supertrend indicator has turned red, MACD lines are still below zero and the histogram bars are starting to flatten. If the price continues to fall, the next support is found at $0.259, which is 27.89% below the current price.
It implies that traders are on the lookout for improvements or more declines. Should the price stay above $0.359, the market mood may calm down, but the current signs suggest being cautious.
Growth Narrative Still Active Despite Price Weakness
Although investors are selling and being cautious right now, some developments in the ecosystem could change people’s opinions.
In just one week, Ethena increased the supply of its USDe stablecoin by $300 million. The previous time a supply jump like this took place, in October 2024, ENA went from $0.25 to $1.25 over a period of two months.
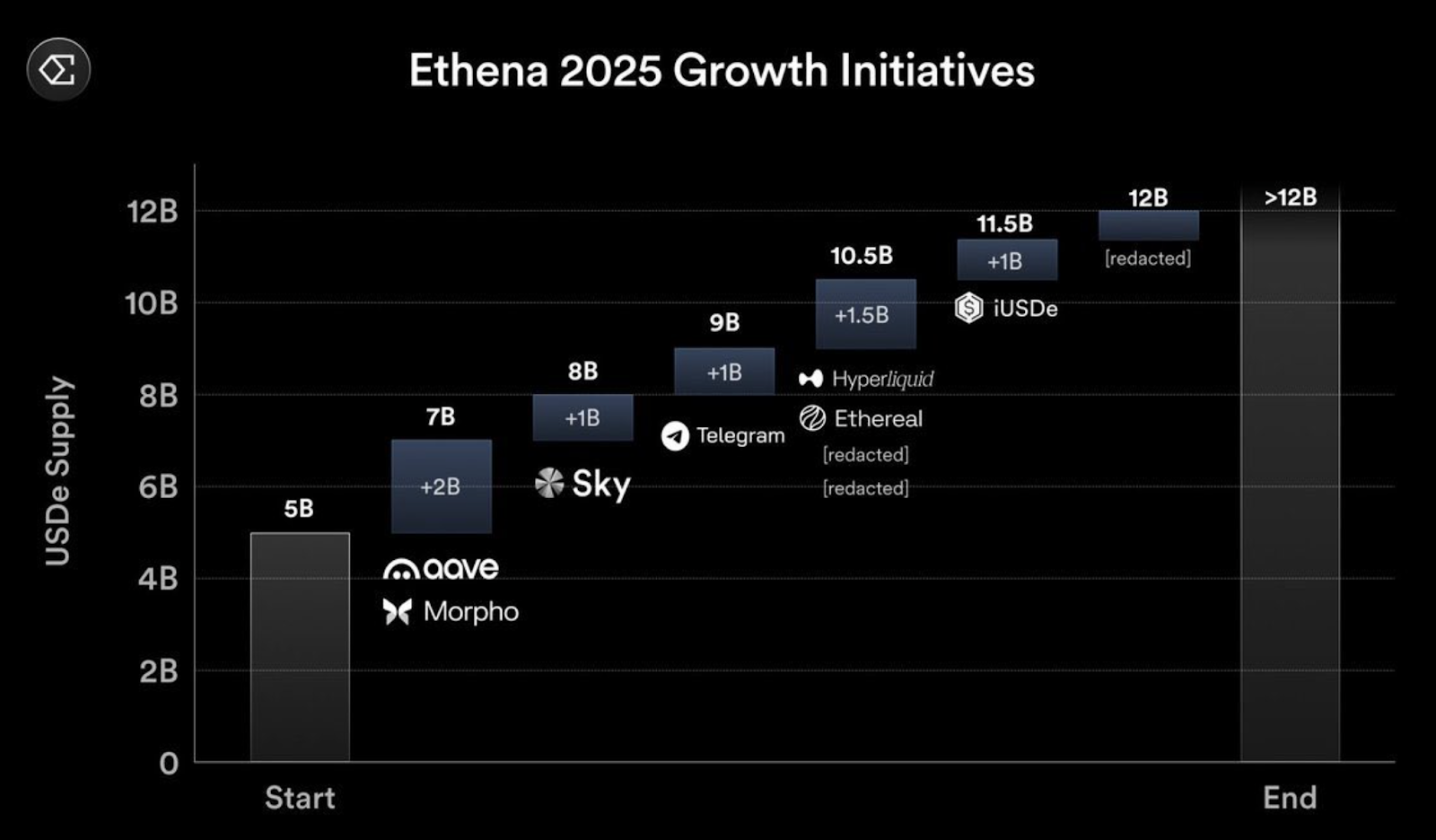
The roadmap for Ethena in 2025 mentions collaborations with Hyperliquid, Telegram and Aave, as well as a new blockchain focused on RWA, launched by Securitize. It is significant that BlackRock is listed as an investor in Securitize, which might attract the interest of traditional finance companies.
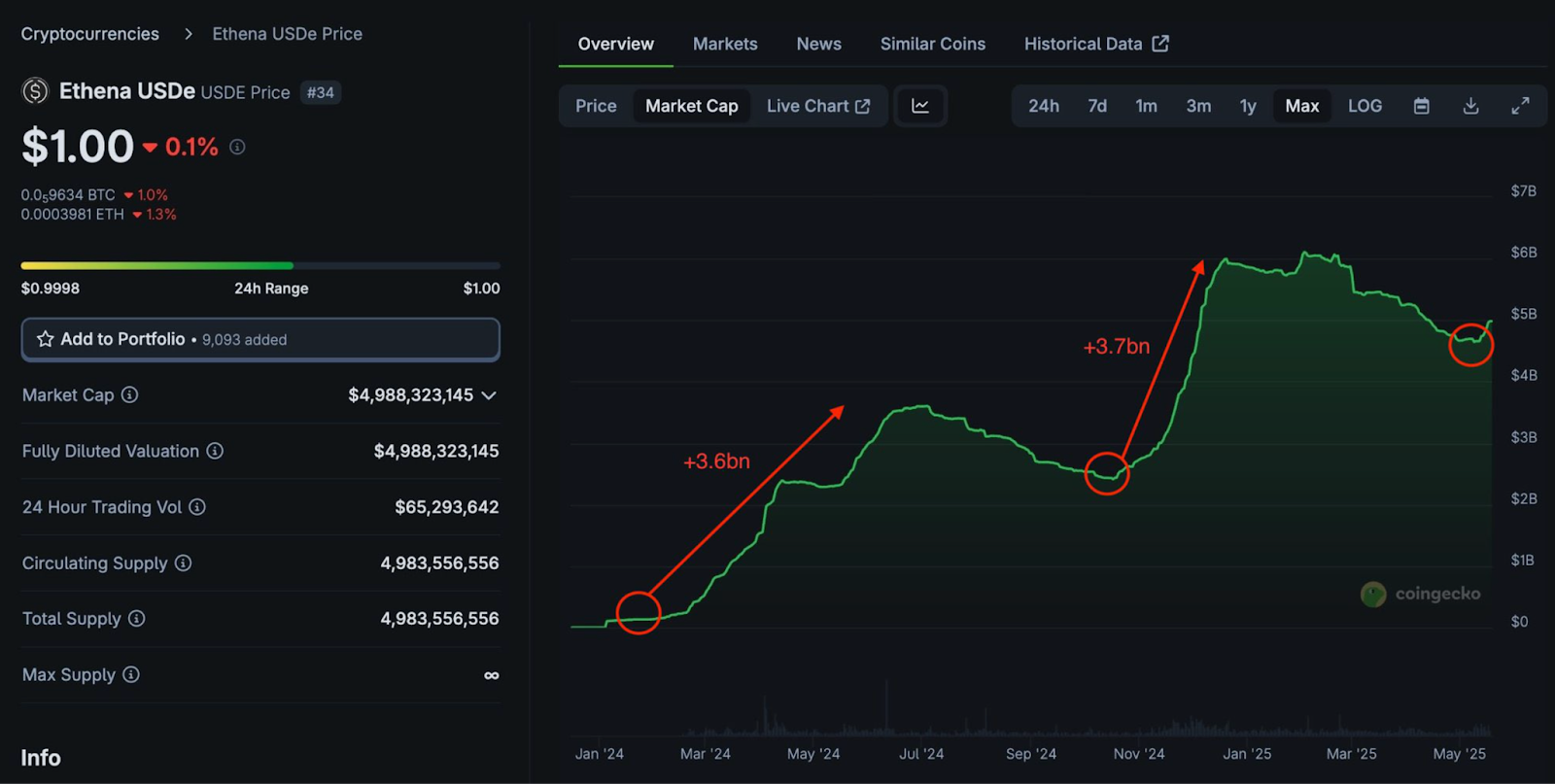
According to CoinGecko, USDe’s value has increased significantly in the last few days. Between January and March 2024, USDe saw an addition of $3.6 billion. The next year, another $3.7 billion was added and the token’s cap is now $4.98 billion.This means the economy is still growing, but ENA’s price is not yet showing that strength.
